
Published
07/03/2025, 11:51According to a study conducted by the Digital Resilience Association (DRA) in collaboration with TSARKA Kyrgyzstan, nearly half of the websites of the country’s banks and microfinance institutions exhibit low level of vulnerability. Out of 26 resources examined, 14 were found to have critical vulnerabilities that could be exploited for data theft and attacks on clients.
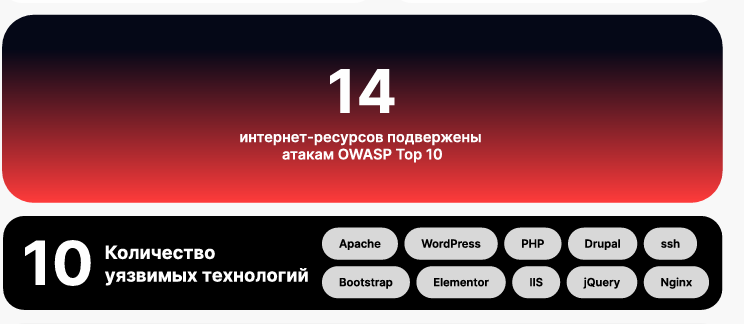
The study revealed a wide range of issues: from open ports and outdated TLS versions to vulnerable subdomains and misconfigured mail servers. The average security score was 71.75%. For the financial sector, where billions of soms and public trust are at stake, this is an unsatisfactory result.
Among the identified vulnerabilities were the absence of basic security headers (such as X-XSS-Protection, Content-Security-Policy, etc.), outdated CMS platforms, access to critical paths like /admin or /config.bak, and a lack of protection against DNS spoofing. Not a single website uses DNSSEC — an international standard that ensures the integrity and authenticity of DNS data.
It was also found that 9 websites still use the outdated TLS 1.2 protocol, despite the availability of more secure versions. Critical CVEs — officially registered vulnerabilities in international databases — were detected on 10 platforms. For example, CVE-2023-40743 or CVE-2021-27023 could lead to complete traffic interception and server compromise.
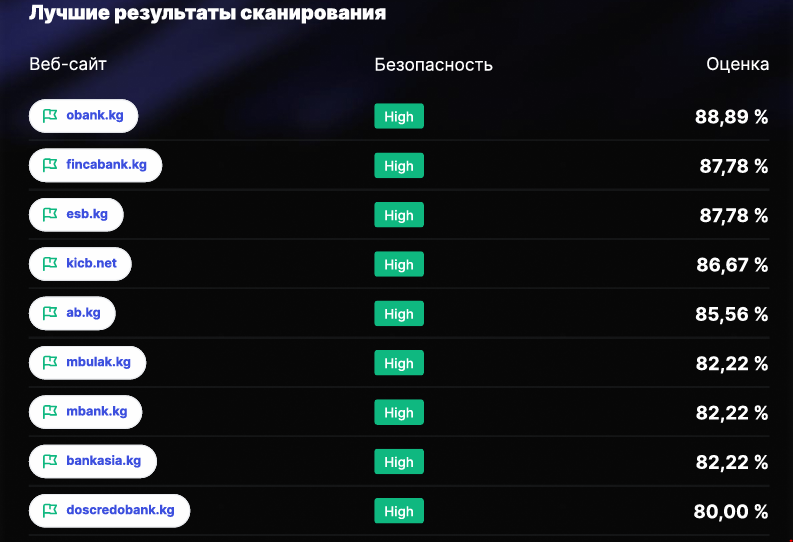
The best performance was demonstrated by the websites obank.kg, fincabank.kg, esb.kg, kicb.net, and ab.kg — their security levels were assessed at over 85%.
“The results of the cybersecurity analysis of Kyrgyzstan's banking sector indicate a trend toward improving information security; however, several web resources were found to have serious vulnerabilities that need to be addressed as soon as possible,” — the study’s authors note. — The main vulnerabilities include misconfigured DNS settings, lack of basic protection against phishing and spoofing, open ports and directories, as well as outdated technologies with known vulnerabilities. Some online resources remain at a minimal level of protection, despite their public significance and the potential risks of data leaks or system compromise.”
Among the recommendations are the mandatory implementation of SPF, DKIM and DMARC on all domains; auditing subdomains and eliminating forgotten test resources; closing non-standard ports; updating CMS platforms and web application components; and installing automated vulnerability monitoring systems.
The importance of appointing cybersecurity officers at the executive level of banks is particularly emphasized, along with the implementation of secure email protocols and regular training for IT specialists.
Experts are confident that this approach can protect the banking system from scenarios where a single configuration error could lead to significant losses. Moreover, it is not only about cybersecurity threats but also about the bank's reputation.



